
You might have heard the term “Phishing” bandied around, and be vaguely aware that it’s something bad guys use to scam you. But you probably haven’t a clue what “Vishing” and “Smishing” are, or even if they’re actually a thing. In this article, Dave explains all of these scammer techniques, how they work and how to avoid falling prey to them.
What is Phishing?
Phishing tries to catch the victim out using disguised email as a weapon. The aim is to get you to click a link or download an attachment.
Phishing emails will usually masquerade as being from someone you trust – your bank, a friend, or an organisation you have done business with. It’s almost as old as the internet itself, dating back to the 1990s. Its longevity as an attack vector means that phishing attacks have become increasingly more sophisticated, and some phishing emails are almost indistinguishable from the real thing.
Why is it called “Phishing”?
It’s pronounced just like it’s spelled, and it’s meant to be an analogy for an angler throwing a baited hook out there (the phishing email) and hoping you bite. The term arose in the mid-1990s among hackers aiming to trick AOL users into giving up their login information. The “ph” is part of a tradition of whimsical hacker spelling, and was probably influenced by the term “phreaking,” short for “phone phreaking,” an early form of hacking that involved playing sound tones into telephone handsets to get free phone calls.
Phishing is a form of social engineering, requiring human interaction to be successful. More precisely, it relies on the insecure part of the email system – the human being on the receiving end.
Phishing is easy for criminals to do – they simply purchase a “phishing kit” from the dark web, install it on a server, start sending emails and wait for the cash to roll in. Of course, they also need a list of e-mail addresses, but these are really easy to purchase from the dark web too. Or they can generate a list for themselves, by just tacking the most common usernames on the front of “@hotmail.com” or “@gmail.com”. Even for someone with very limited programming skills this is a 5-minute job.
Types of phishing attacks
Generally, a phishing campaign tries to get the victim to do one of two things:
- Hand over sensitive information. Usually with these the aim is to get you to hand over your username and password so they can log into one of your accounts. Typically, you’ll receive an email from say, your bank, telling you that you need to reset your credentials, with a link to click on to do so. The email will be convincing enough that most users will click the link, and they will then be taken to a spoof website that looks close enough to the real thing that they are convinced to type in their details. Of course, all the website is doing is harvesting the login credentials, and these are then used to login to your account and siphon away your cash. The attacker will usually send millions of emails out, in the hope that a few users will be tricked. A 1% return on a million emails is still 10,000 victims!
- Download malware. The aim here is to get the user to infect their own computer, often with a “back door” or “keylogger” that will record what you do. More commonly, the infection is “ransomware” – the malware will lock your data with strong encryption, and a pop up will demand a cash sum to unlock it. Even worse, if you use a credit card to pay them the ransom, they will often use your credit card details to rob you again! The most common way is to get you to download an attachment, usually a .zip file or a Microsoft Office document.
Phishing emails can also target specific groups of users, rather than just being sent out randomly. The attacker might have obtained a list of email addresses from a service that has been hacked (see the “Have I been pwned” website for a list of recent hacks and the data that was obtained). They will then set up their phishing attack so that the email looks like it comes from one of these websites, and if you’re a customer or registered user you’re more likely to trust it.
More often than not, the phisher will simply choose a trusted brand and spoof their email to look like it comes from them, in the hope that a small percentage of users are actually customers and will fall for it. Again, 1% of a million is 10,000. VadeSecure.com publishes a list of “Phishers’ Favorites” (sic) each quarter. You’ll note that PayPal is #1, hence my advice in a previous post about turning on 2 Factor Authentication when you set up PayPal.
What to look for
A phishing email will often have one or more of the following features:
- Too Good To Be True – “You have won an iPhone – click here to claim your prize!!” You haven’t. In fact, you didn’t even enter a competition. Don’t fall for it!
- Sense of Urgency – “Only 1 hour left to claim this exclusive offer!” Nope. I don’t need it, whatever it is. Especially not ‘cosmetic enhancements’…
- Hyperlinks – there will almost always be a hyperlink in the email. And if you hover over it, it will look like someone has poured a tin of alphabetti spaghetti on your computer screen –jkfj\jsfklfkjfjklafajklfajksfasdjk.com! And if there isn’t a link there will be:
- Attachments – usually the text of the email will say something like “You have to read this file I sent you”, or “Take a look at this hilarious video”. Remember, this is social engineering. If you feel curious about it, it’s probably bad news! Usually the file will be a .zip file, or a .doc, or sometimes a .pdf. These are what is known as “Trojans”, as referred to in my post about social engineering – they are hiding something nasty!
- Unusual Sender – often you will think “why is this person sending me this?” That’s a prime indication that the email is a phishing attack, even if it’s someone you know.
I actually had an email from a customer today, who sent me the email below as they were suspicious about it. They did exactly the right thing as it’s an obvious scam. The email was sent to their Hotmail address… from their Hotmail address! Immediately suspicious! If you examine the screenshot below you will also notice the things I have circled in red:
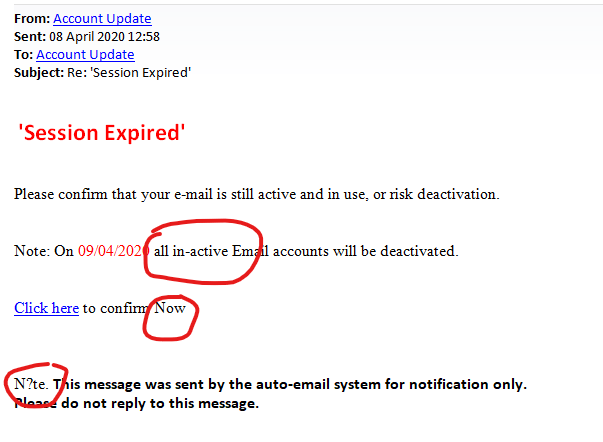
- The word “in-active” is spelled wrong.
- Inconsistent capitalisation.
- The word “N?te” (I think this should say “Note”)
The other dead giveaway was when I pointed my mouse pointer at the link, the address (which I have taken a screenshot of so you don’t accidently click it and end up being scammed) was VERY suspicious:
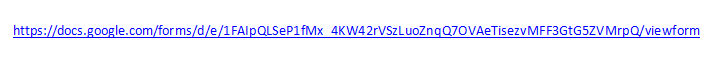
Notice the alphabetti spaghetti?
Because I know what I’m doing, I clicked on the link to see where it went (don’t try this at home kids!) Here is a screenshot of the web page it took me to:
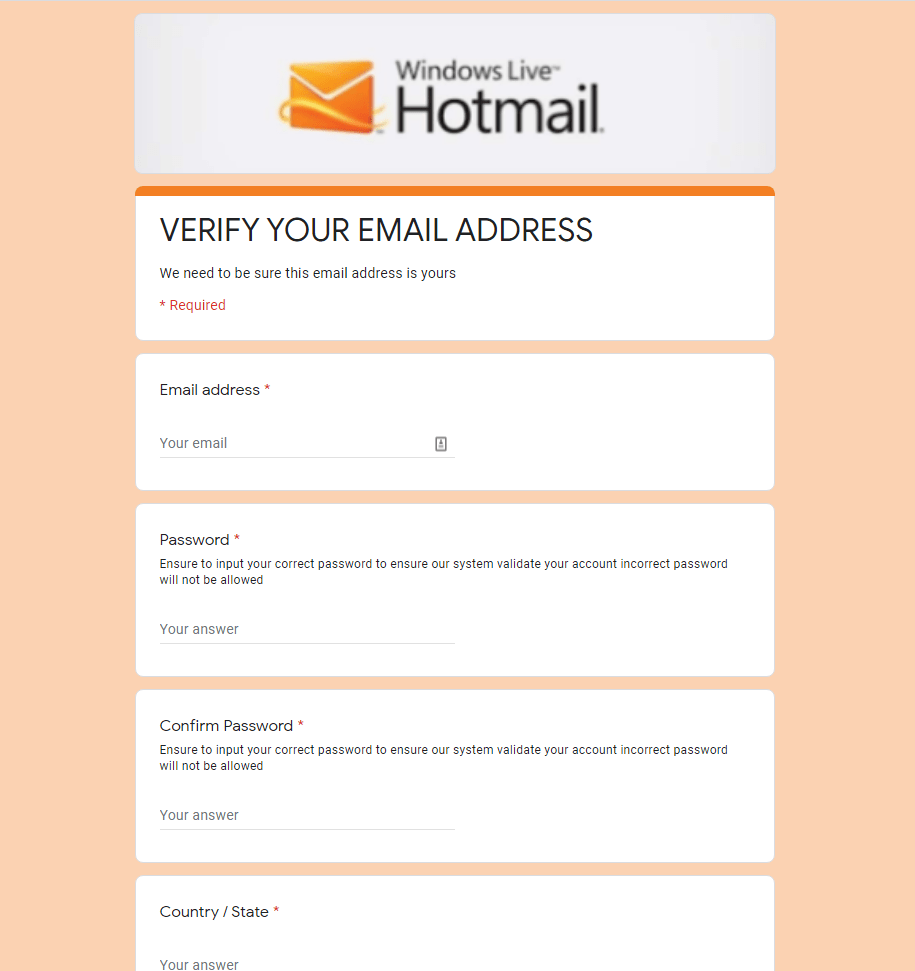
Notice the poor quality image at the top? Note the poor grammar?
This isn’t even a very good phishing attempt, but you get the idea. Oh yeah, and it’s a Google Docs form – why would Microsoft be using that when they are one of the richest corporations in the world?
I’ve had a phishing email – what do I do?
Delete it. Simple as that. If you ever get a phishing email that’s more convincing than the example I’ve shown you, but not convincing enough that you aren’t suspicious, you could check with the people who it supposedly comes from. If it’s your bank, give their customer services a ring. They’re really keen that people do for stuff like this so you won’t be wasting their time. Or you could open your browser and manually type in the bank’s web address, then log in using your secure browser (what do you mean you aren’t using one? I guess I need to write another blog post about that, then…), and check that everything looks OK. Check your bank balance just to be sure. Then change the password on your email account, just to be on the safe side.
More convincing phishing attempts will make some attempt to hide what they’re doing (not like the doofus who sent my example). The web address will look very similar to the one it’s spoofing, for instance www.bar.clays.com. Don’t worry, that’s an innocuous site that sells windows…
But the point is that you do need to watch what you’re doing. Think before you click. A good paid-for antivirus package will have an anti-phishing module built in, but your best protection is vigilance.
What is Vishing?
So you might have heard of vishing, you might not. In short, it uses the telephone to scam you rather than an email. A caller will say they are from a well-known company, and try to talk you into either giving up your personal details, or if they’re really good, installing some “remote access” software on your computer.
I recently had a call from a customer who had been taken in by this. They were told that their Amazon account had been compromised and that they needed to allow the caller to log in to their computer to check that everything was OK. Luckily, my client got suspicious and hung up the phone, but not until they had given away some personal details. That turned into quite an expensive exercise, as I spent a few hours wiping their PC and re-installing Windows to make sure we had eradicated any malware (often the safest way to do it), and another couple of hours going through all of their accounts with them and helping them to change all of their passwords.
Sometimes the call will be an automated message that directs you to key in or say your credentials. Or sometimes you will be directed to call a number, but with the same aim – you will be asked for your credentials. Every year scammers try this by pretending to be from HMRC and saying you owe unpaid tax, and that you will incur penalties if you don’t act immediately. Notice the sense of urgency and the fear factor. Social engineering in action!
I’ve had these myself, they’re very annoying. Most amusing is when someone calls me from Microsoft to say that I have a virus on my PC, and they need to install “specialist software” to clean it up for me. After a few minutes of pretending to be the dumbest user in the world they get fed up and hang up on me. Usually, I haven’t even got up off my couch!
What about Smishing?
Smishing is a relatively new phenomenon, but it simply uses text messages (SMS – hence “smishing”). The same rules apply as those that apply to phishing and vishing. Don’t click any links, don’t call any number without looking it up first, and look for indications that it might not be from who it purports to be from. A good indication of this is that it will come from a 5 digit number rather than a mobile number.
Scammers are counting on people being less sceptical than they would of an email and not looking too closely. A message like “Hey, this is your wife, I just got a new phone—what’s your national insurance number again?” should ring alarm bells.
If you get a “fraud alert” that says it’s from your bank, don’t tap the link in the message and sign in. Instead, go to your bank’s website directly or call your bank on the phone and ask if the alert message was legitimate.
Report it!
You can, and should, report a suspected phishing, smishing or vishing scam to Action Fraud over the phone using the number 0300 123 2040, or click to go to their website. It’s your duty to do so, in order to protect others. In the meantime, stay at home and stay safe!
