
I have been contacted by at least 2 people over the last week, both of whom were extremely concerned. They had received an email with the following text (or similar), and didn’t know what to do about it. In this post, I’ll explain why this scam is nothing to worry about, and some steps you can take to make sure you’re safe. Here is what they received:
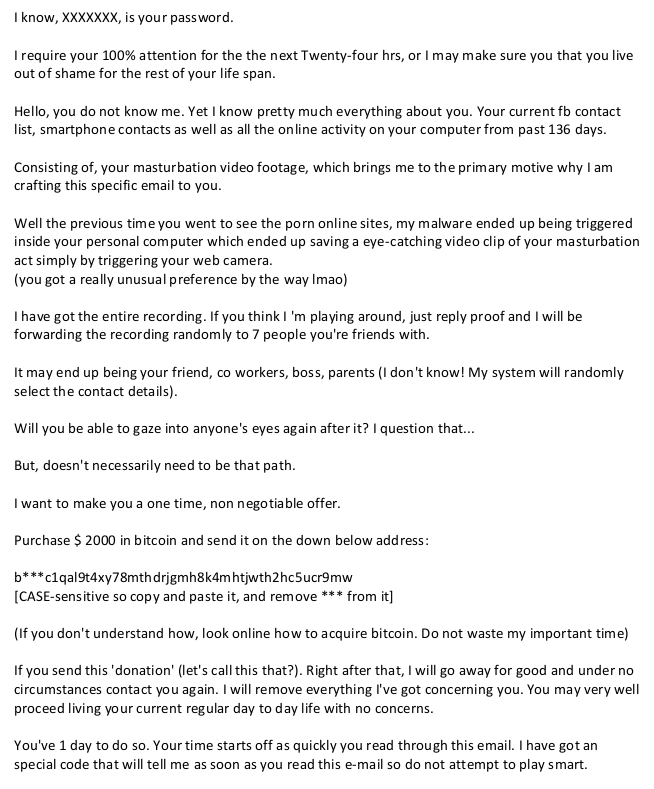
This is a relatively old and common scam, just with a new twist. I’m going to break it down and explain each part of this attempt at blackmail, and along the way you’ll learn a few things, such as:
- How do they know your password?
- Can they really access your Facebook contacts?
- Have they really got ‘candid’ video footage of you?
- What the hell is a ‘bitcoin’?
- What should you do now?
How do they know my password?
“I know, XXXXXXX, is your password.“
Every so often, a hacker will manage to break into the servers of an online service such as Facebook, Hotmail etc. Once they’re in, and if they aren’t detected for a while, they’ll be able to get hold of the database that contains the usernames and passwords of everyone who has an account with them. With Facebook and Hotmail, the username is the email address, so the hacker has hit the jackpot – he now has a list of all the accounts and passwords, but also the email addresses of all of the owners of those compromised accounts.
What happens next depends on the organisation that has been hacked. Most sensible organisations won’t store your password at all. What they will do instead is store a ‘hash’ of your password. When you first join the service and are prompted to enter a password, the website does some work behind the scenes. The software will run an algorithm that effectively turns your password into a number. The next time you log in, the software carries out the same algorithm on the password you enter, and if the number the service has stored for you matches, it means the passwords match and you are granted entry.
This process makes it harder (but not impossible) for the hacker to crack your password. So what usually happens is that they will sell the database on to other criminals, or even just ‘dump’ it on the internet for a laugh.
Sometimes though, the passwords are stored in ‘plain text’. In other words they are readable just by looking at them. No hashing, no encryption, just dumbness and carelessness on the part of the service provider. The hacker can then use this readily available data to launch an attack. Or they are just as likely to sell it on to a third party. Or dump it on the internet for a laugh.
I wrote a post a couple of weeks ago about choosing a strong password, with some illustrations as to how long it would take to crack them if they had been encrypted. If you’ve read that post, it will be no surprise that the 2 people who contacted me had chosen passwords that were REALLY easy to crack. According to the online tool I referred to in that post their passwords would have taken 0.18 seconds and 30.61 seconds, respectively. So they might as well have not bothered. And that is how the ‘blackmailer’ knew their passwords!
Can they really access my Facebook contacts?
“I know pretty much everything about you. Your current fb contact list, smartphone contacts as well as all the online activity on your computer from past 136 days.”
In theory, if they have your username and password for Facebook then, yes, they can access your Facebook contact list. It’s highly unlikely they can access your smartphone contacts – they would need to get you to install a further piece of malware to do that. And it’s just as unlikely that they have all of your online activity for “136 days”, unless they also got you to install some malware on your computer.
Now, installing malware on your computer could be as simple as getting you to click on a link in an e-mail. But many online porn sites are also vectors for infection – they rely on the person not to report any criminal activity that happens as a result of them accessing content they would be ashamed of admitting to.
So I guess it’s down to how likely it is that you did visit a porn website that might have installed some malware. You didn’t? Don’t sweat it. You did? If you’re into that sort of thing you need to be more careful, or at least have a good suite of anti-malware software! I’ll be doing an “Anti-Virus Showdown” post in the future to help you choose.
But the thing to remember is that this is just a bluff. There aren’t many of us that can truthfully say they’ve never engaged in… self-love… while watching porn. And that’s what the hacker is counting on.
Have they really got ‘candid’ video footage of me?
“Well the previous time you went to see the porn online sites, my malware ended up being triggered inside your personal computer which ended up saving a eye-catching video clip of your masturbation act simply by triggering your web camera.
(you got a really unusual preference by the way lmao)”
Again, probably not. They would need to install some malware that not only captures the video feed from your webcam, but also sends it to the hacker’s computer. While tools to do this are readily available off-the-shelf (indeed, some professional tools are available to do it – see this report from 2010 about some “anti-theft” software installed by a US school on its laptops that was allegedly used to spy on students), in order to make use of them the hacker has to get them on your computer. Any guesses as to how they will do this? That’s right – they get you to click on a link or download a ‘Trojan’ that activates the malicious code.
So as long as you follow the advice in my previous post about NEVER clicking on links in emails from people you don’t know or trust, you should be safe from this one.
Many paid-for Anti-Virus programmes include ‘webcam protection’, where you can disable the webcam unless a particular program is using it such as Skype or Zoom. I use Kaspersky Total Security to manage my online security, but as I said, I will do a roundup of Anti-Virus packages in the near future. In the meantime, there is some good advice about securing your webcam here and here.
What the hell is a ‘Bitcoin’?
It’s a good question, and it also leads to a second question – why do hackers insist on being paid in Bitcoin?
The full answer is long and complicated, but if you’re really interested you can read this series of articles, or watch this series of videos. In essence, though, Bitcoin is a digital currency – it’s generated by computers using an algorithm and there are all sorts of clever tricks done with encryption to ensure that the currency can’t be faked. As with all currencies, the issue of trust is important. But it’s even more important with Bitcoin, as there’s no centralised authority that issues it – anyone can ‘mine’ Bitcoin using their own computer. It’s this lack of a centralised authority that attracts criminals to Bitcoin. It makes the transactions harder (although not impossible) to trace, and they can use pseudonyms or anonymous accounts more easily (although law enforcement is getting better at identifying these accounts).
The other reason hackers like Bitcoin is that the transactions are irreversible – once you’ve bought or traded a Bitcoin it’s very difficult, if not impossible to get your money back.
Of course, as law enforcement finds new ways to catch online criminals using Bitcoin, they are looking at other ‘cryptocurrencies’ to do their dodgy deals.
What should I do now?
Don’t Panic! It should be clear from reading this post that the person who sent you the email is an opportunistic blagger, trying to bluff their way to some easy money. But you still need to do some stuff to make sure you’re safe.
- Have a little chuckle at the desperation of it all.
- Check and change your passwords. Go to ‘Have I been pwned?’ (why ‘pwned’ you ask? See here for the answer to that). Enter an email address or a password that you think might have been compromised. Look on in horror as it is revealed that your details have been found in one of the thousands of data breaches that have occurred since you started using a computer. Change the passwords on each compromised service, and any that are linked to it. Start using a password manager like LastPass so you don’t get caught out using weak passwords again (future blog post coming up).
- Put some masking tape or a Post-it note over your webcam. Especially when you’re ‘watching’ porn…
- Download and install an anti-malware program that includes webcam protection (future blog post coming up).
- Report it. Report the attempted fraud to ActionFraud. Even if they don’t catch the little beggar, they will be able to trace the source of the email and get the ISP to do something about it. You can also report the abuse of the Bitcoin by copying and pasting the code that the blagger has helpfully provided.
- Bin the email, after adding it to your Spam Filter.
That’s all for now. Stay home, stay safe.
